PROFESSIONALCOMMUNITY
Testing for reflected XSS using Burp Repeater
-
Last updated: July 6, 2023
-
Read time: 3 Minutes
XSS vulnerabilities can arise when user-controllable input in an HTTP request is "reflected" in the resulting response in an unsafe manner. Burp Repeater lets you directly manipulate HTTP requests without interference from client-side controls, and makes it easier to test whether reflected input is being adequately sanitized or filtered server-side.
In this tutorial, you'll learn how to:
- Use Burp Repeater's search and auto-scroll features to quickly identify reflected input within a response.
- Identify and exploit a basic reflected XSS vulnerability.
- Replay a request from Burp Repeater in the browser to see your attack from the victim's perspective.
Step 1: Find an interesting request
Using Burp's browser, access the following lab:
https://portswigger.net/web-security/cross-site-scripting/reflected/lab-html-context-nothing-encodedOn the deliberately vulnerable blog website, use the search bar to search for an arbitrary, distinct string. This is commonly known as a "canary".
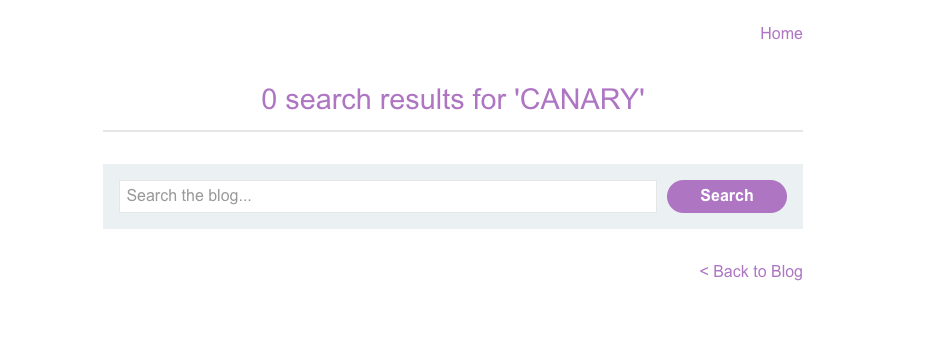
As you can see, our search term is displayed on the results page. We'll use Burp Repeater to test whether this reflected input is being properly sanitized by the server.
Step 2: Send the request to Burp Repeater
As you have been using Burp's browser, you can view the history of your HTTP interactions with the target site on the Proxy > HTTP history tab.
Find the GET /?search=CANARY request that was sent to submit your search query. Right-click the request and select
Send to Repeater.
Step 3: Search the response for your reflected input
Go to the Repeater tab, where you can now see the request in a numbered sub-tab.
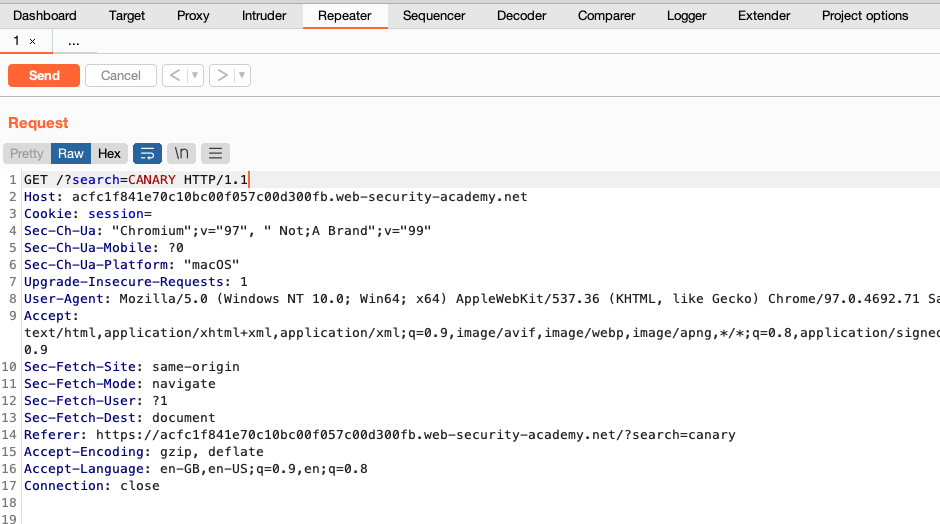
Click the Send button to resend the request. The resulting response from the server will appear in the Response panel.
Use the search bar at the bottom of the Response panel to search for any occurrences of your canary string within the response.
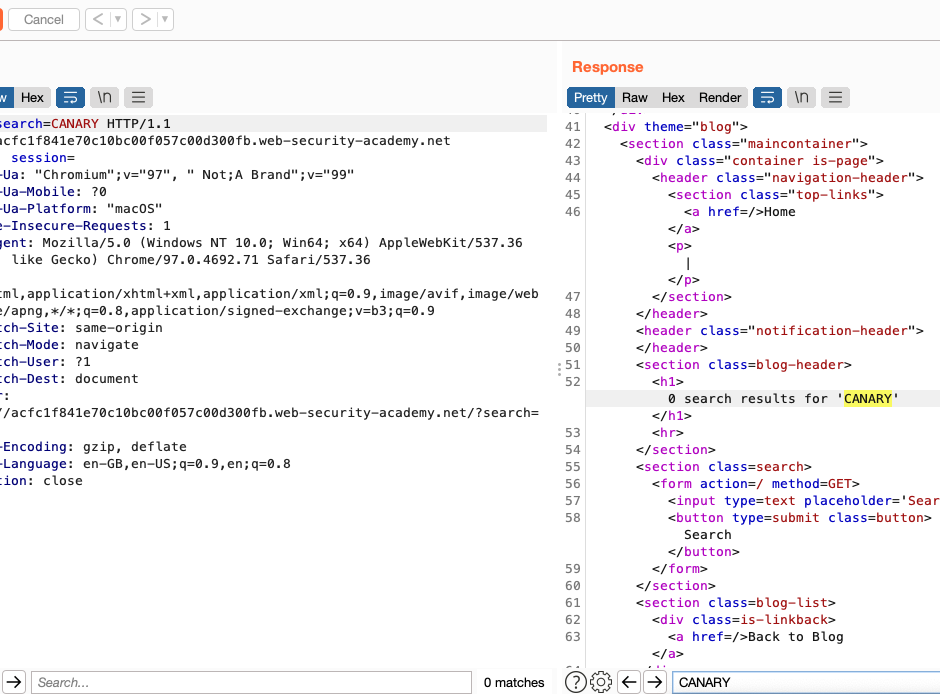
Step 4: Identify the injection context
In the response, study the surrounding context in which your input is reflected. This affects the potential XSS vectors you can use to construct an attack. In this case, we can see that our input is reflected inside an HTML <h1> element.
Step 5: Test for flawed input sanitization
In the request, add an opening <script> tag to the value of the search parameter. We'll use this to test whether < and > characters, or the entire tag, are being properly filtered or sanitized by the server.
In the bottom-left corner of the Response panel, click the cog icon and select the Auto-scroll to match when text changes option.
Send the request and observe that the panel now automatically scrolls to the line where your canary string is reflected. Notice that the <script> tag is not being stripped or escaped in any way.
Tip
You can use the < and > buttons at the top of the Repeater panel to step back and forth between requests. This is especially useful when combined with the auto-scroll option.

Step 6: Send an XSS proof of concept
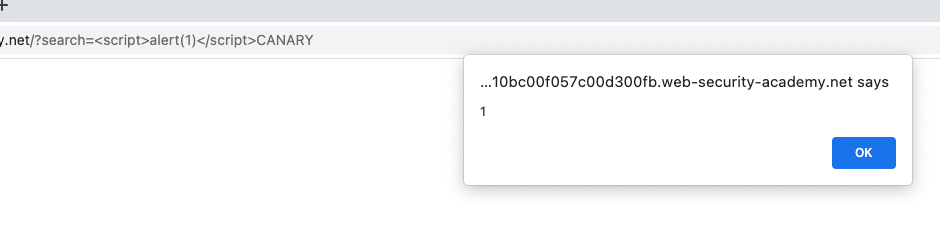
In the request, change the value of the search parameter to a full XSS proof-of-concept attack, such as <script>alert(1)</script>CANARY, and send the request.
In the browser, notice that the lab is now solved. If you want to confirm that the payload executes, right-click on the request in Burp Repeater and select Show response in browser. Copy and visit this URL in the browser and observe that the alert() function is called successfully.
Summary
Congratulations, you have learned how to use Burp Repeater to test for and confirm basic reflected XSS vulnerabilities. You have also learned how to use Burp Repeater's search and auto-scroll features to speed up your workflow when testing how different input is processed by the server.
Read more
If you want to read more, then check out the subject on our web security academy:


